A common technique, used by malicious attackers to fool their victims, is using the Unicode special character U+202E known as an annulment from right to left to make the malicious file appears as a PDF document instead of a potentially dangerous executable file.
To understand this concept, let's imagine that our malicious file is "document.exe" (see Figure 1):
Figure 1: Malicious file recently created with no changes.
Now we are going to follow the steps below to accomplish our goal:
- Open the Windows Character Map (Start, Run, charmap)
- Find and Copy the Unicode character U+202E. Notice that at the bottom left shows the ASCII value of the characters (see Figure 2).
Figure 2: Charmap with U+202E selected and copied.
- Paste (Ctrl + V) the character just before the extension point: "document[[U+202E]].exe"
- Enter the extension that you want but in reverse, for example, if we want "doc", we need to write "cod", or if we want "pdf", then we need to write "fdp".
Figure 3: Malicious file renamed with the special character.
(The real name of the file without the special character should be: "documentfdp.exe")
Finally, to perfect the infection vector, a good idea would be to change the icon of the malicious file and also use a name that can trick the user, considering that the "exe" or the original extension must remain. E.g.:
Figure 4: Malicious file disguised as a Microsoft Word file, with a tricky name in order to preserve the original extension and fool the user.
The malicious file is ready to be delivered to the target and the following happens:
Figure 5: Common Infection Flow (TrendMicro)
If the victim executes the malware (Double Click or Enter), the following screen would appear:
Figure 6: Malicious File starts a command prompt and shows a message: "Hello World".
Now, let's look at the title of the shell: "annexe.doc", apparently our technique is almost perfect because we can't see the original extension even in the command line, or we can?
Possible Countermeasures:
- If we try to rename the file (F2), we will see something strange, this effect is produced by the special character, so this is a clue to realize that something is wrong.
- If you are in a GNU/Linux based system, you can check the headers of the file with some commands.
- Another trick that you can use to verify the name of any file and its extension could be using the command prompt, but how?
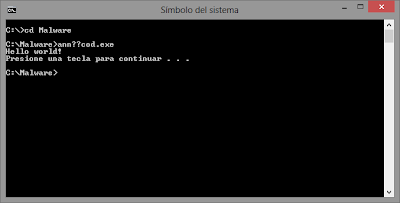
To prove this theory we need to open a new "cmd.exe" in the location of the suspicious file, after that, we write the first two characters of the name and press "Tab", the system will autocompletes the true name, then we will know the truth!! (See Figure 7).
Figure 7: Revealing the true name of the suspicious file and executing it.
As shown in Figure 7, the name of the file has (one or more) strange characters that aren't recognized and are shown as 2 question marks, revealing the presence of the "U+202E" character, that's all, hope you like this post. =)
Source of Figure 5: http://blog.trendmicro.es/bot-zeus-y-conexion-kneber/



















0 comentarios:
Post a Comment